 Yesterday, Rudder suffered an embarrassing email glitch that affected 732 customers. In the pre-Internet days, no one other than those few hundred customers, and a few of their friends, would have heard about it. Even in the days before blogs became common, pre-2007, it’s unlikely the story would have made it to the mainstream press.
Yesterday, Rudder suffered an embarrassing email glitch that affected 732 customers. In the pre-Internet days, no one other than those few hundred customers, and a few of their friends, would have heard about it. Even in the days before blogs became common, pre-2007, it’s unlikely the story would have made it to the mainstream press.
And even last year, before Twitter, the story might have died without ever crossing over to the mass media. But when it comes to breaking news and company gaffes, it’s a whole new ball game. Everyone wants 15 minutes of fame as an investigative reporter, and Twitter is the dream platform.
I’m going to recap the problem, and how the news broke, in excruciating detail, because it illustrates the power of Twitter- and blog-fueled grassroots reporting. If you are a financial services company, think about how you could use social media to help with damage control should something similar happen to you.
What happened at Rudder
According to the detailed description first published in TechCrunch and then later published by the company on a new blog created specifically for this issue, an email upgrade the night of May 18 caused 732 users to receive dozens of email updates containing balance and transaction information of other users. Only Rudder users with email addresses that begin with “a” or “b” received the erroneous emails because the company stopped the email job at that point after realizing the “upgrade” had gone terribly wrong.
Besides seeing the info in the email updates, the bigger security/privacy problem was that unauthorized users were able to click through email links to access the full aggregated account at Rudder.com (see screenshot in the TechCrunch article). However, at no time could anyone actually log in to anyone’s bank account or move money in any way.
Luckily, Rudder, like all account-aggregation companies, does not include account numbers or personal details in the updates. However, the email addresses of each user was displayed, so any of the 732 customers using an email address at Rudder that can be traced back to their real name, had their financial details exposed to hundreds of users.
How the news broke
At 5:36 AM yesterday (19 May), Twitter user @adambassador tweeted this:

And @adambassador didn’t stop at that. He took the time to search and communicate warnings directly to several other users who’d recently mentioned “Rudder.com” on Twitter. Adambassador would go on to tweet 21 times yesterday about the Rudder problem.
One of the people who heard from @adambassador was financial services consultant and blogger, Mike Linskey (@mikelinskey) who’d just Tweeted about several of the PFM companies he’d seen at our FinovateStartup conference, including Rudder.com. Mike then posted the problem to his Fincision blog at 8:04 AM, and at Mike’s request, adambassador posted screenshots of the emails to document the problem, which were then published in Mike’s blog entry.

At 10:05 AM, using Twitter, Mike alerted the blog Mashable about the Rudder problem. A half-hour later, Mashable, the fifth largest blog in the country (see note 1), posted the story citing adambassador’s tweets and Mike’s blog entry. From the Mashable blog entry (below), the problem was retweeted 115 times (see the retweet button below on left).

Then at noon, the second largest blog, TechCrunch, with more than 2 million subscribers, posted the story. And because of high comment activity, it stayed on the top of TechCrunch most of the day (see screenshot below), generating 58 comments.
How Rudder handled it
By almost any standard, Rudder did a good job responding. Although their reply took more than 10 hours since the error was first reported on Twitter, Rudder’s CEO posted a detailed comment on the TechCrunch (scroll down to his comment at 4:38 PM here) and Mashable posts, apologizing for the error and explaining in great detail what had happened.
In addition, Rudder created a special “Rudder Update” blog (see screenshot below) apologizing, explaining the mishap and exactly what info was mistakenly displayed, and detailing the steps they were taking to fix the problem and help affected customers:
- Turned off the email system entirely
- Contacted each affected user individually and offered them a complimentary subscription to an identity theft service
- Engaged an independent security auditor to survey its system and look for weaknesses
- Published a URL for users to go in and delete their accounts if desired
Analysis
Rudder did a good job considering the situation. It was smart to comment on TechCrunch and Mashable, and the new damage-control blog site was a savvy move. And the company did an exceptionally good job with the tone and wording of its mea culpa.
That said, the company could have used social media better. The company’s Twitter page (@userudder) and that of its CEO (@nikhilroy) were silent all day. A short Twitter posting, even “we’ve stopped all emails and are working on it” would have reassured users and potentially made the Mashable post less alarming. Also, the company didn’t have a blog, so there was no place where they could post periodic updates during the day. It was complete silence for 11 hours, other than the interview with TechCrunch’s Erick Schonfeld mid-day.
Impact on third-party PFM credibility
While this was embarrassing and violated the privacy of several hundred users, there will likely be no financial loss to anyone. There was no data breach or stolen account numbers. Even a single bank account statement stolen from a mailbox could cause more potential financial damage.
And even though third-party PFM providers have had a relatively spotless record for security/privacy, this mistake, now well-documented in two of the largest online publications in the world, will be cited in the media for years, to cast doubt on the security of online personal finance.
It might cost the industry a point or two in short-term market share, but it would take something much worse to materially slow growth. Even Rudder should be fine. By addressing the issue in a highly professional way on the same day, most customers will be reassured, at least those that weren’t directly impacted.
The bigger lesson here is the need for damage-control procedures that take into account the power and speed of new media (note 3). The entire episode could have—prior to Twitter and the blogosphere—been known to just a few hundred customers of a very small company, but instead traveled from a lone tweet to a large splash across the homepage of a major publication, all within a 6-hour period.
TechCrunch featured the Rudder post on its main page most of the afternoon (19 May 2009)

Special damage control blog created by Rudder yesterday
(19 May 2009; link)

Note:
1. Ranking by Technorati authority (here)
2. Thanks to Mike Linskey for the tip yesterday morning.
3. Also, account aggregation users should use an email address that is not directly associated with their name.
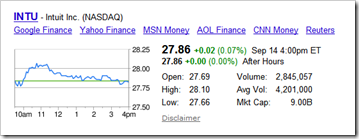
 I was poking around the various small business online accounting sites today researching our next Online Banking Report and thinking about which service would suit our business, given that Microsoft is pulling the plug on Money.
I was poking around the various small business online accounting sites today researching our next Online Banking Report and thinking about which service would suit our business, given that Microsoft is pulling the plug on Money. 









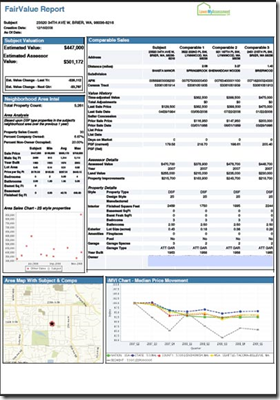
![clip_image002[8]](http://s3.amazonaws.com/finovate-archive/old/WindowsLiveWriter/LowerMyAssessment.comLauncheswith125Fee_E0C1/clip_image002%5B8%5D_thumb.jpg)





















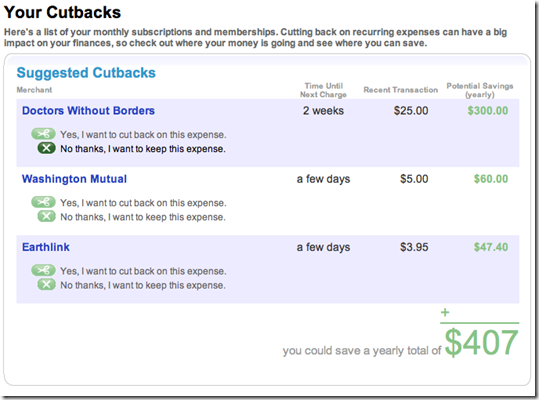
 We’ve regularly cited
We’ve regularly cited