Most banks around the country are busily complying with the Federal Financial Institution Examination Council’s (FFIEC) mandate that they switch their online banking sites to two-factor authentication this year. Playing out against the past year’s flood of identity thefts and data breaches, it’s a necessary and welcome step that will help banks recapture customer trust in the online channel.
Rolling out a new feature is typically as important as choosing one, though, since a clumsy, error-rich rollout can be about the worst marketing tool going. What to do? Take a page from Bank of America’s rollout of its SiteKey authentication system, says TowerGroup senior analyst George Tubin.
“The industry should look to this rollout as a model for implementing consumer-facing technologies,” says Tubin. ”BofA, being who they are, is very adept at implementing them, and they parlayed that into this rollout.”
The key to BofA’s success with SiteKey—launched in collaboration with PassMark Security Inc.(acquired this week by RSA Security Inc.)—was flexibility, says Tubin. “Whenever you implement anything for consumers, you have to focus on the lowest common denominator,” he says. “Some consumers are very adept at picking things up quickly, but there’s always going to be a segment that doesn’t get it, and when you design these things, you really have to focus on that bottom ten percent of your customer base. The main thing is to recognize that not every idea is easy to understand.”
The bank had already quantified how much they had to lose by doing nothing, and decided to act before security concerns caused attrition, or an actual exodus, among its 15 million online customers. But instead of deciding what was best for their customers and acting by fiat, BofA began conducting focus groups in 2004, focusing on finding an approach that worked, but that was easy for customers to use. It was conducted like a sort of police lineup, with focus group members given various authentication systems to try, but little bank input.
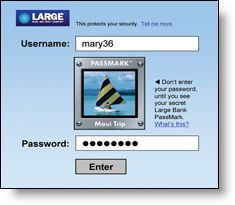
This gave the bank a good handle on what made a system that would be easy to use and well received. One of the results of this exercise: The bank-designed “watermark” that shows up on user’s screens when they log on to the bank’s website. The watermark got high marks for, among other things, letting customers know the bank cared about security without asking too much of them.
The bank realized that a good authentication system needed to be as invisible as possible, a perception that led them to use risk-based authentication. Risk-based authentication combines identifiers like ISP, computer type and operating system with the customer’s PIN number and other identifiers and thereby quantifies the probability that the customer is who they say they are. The registration and subsequent log-on process create a hedgerow of challenge questions, secure cookies, and other security factors, chosen in collaboration with the customer, that reinforce both the real—and apparent—site and customer security.
The bank was willing to build its own risk-based system—in late 2004 there were only a handful of companies that could deliver a practical system—but chose PassMark after the RFP process. PassMark had already installed a system with the Stanford Credit Union, and that gave it more experience than its competitors.
Then came the December, 2004 rollout, which was incremental, highly publicized, and built for speed. Sanjay Gupta, BofA’s e-commerce executive, wanted the rollout to be finished in half the time such massive projects usually take. The bank got there by taking a “test and learn” approach, initially using bank employees for a voluntary test drive in April 2005.
The data from that test drive was followed by a series of mini-rollouts around the country. This gave the bank time to discover and correct problems when they were still small, avoiding the possibility that unnoticed glitches could become big headaches in a mass rollout. The idea worked: BofA now runs three SiteKey sectors—for California, the Northwest, and the rest of the country.
The bank’s success probably helped the FFIEC bite the bullet on mandating two-factor authentication for all banks, thinks Tubin, who cautions newcomers to be prepared for spikes in call center activity related to implementation when rolling out a two-factor authentication system. He recommends banks take advantage of that phenomenon to harvest feedback from users, allowing the bank to adjust their rollout accordingly. That might mean some training for call center personnel, but the training bill is likely to be significantly cheaper than correcting mistakes before they get big.
BofA also discovered that some customers just don’t take the registration process seriously—leading to forgotten challenge questions, for instance—and that they benefited from employing some fuzzy logic in accepting the answers, since customers don’t always remember the exact form of a challenge answer.
As a result of their experience, says Tubin, BofA incorporated two new security features in 2006: A BofA-licensed version of Earthlink’s ScamBlocker on their toolbar, which alerts users when they’re accessing dangerous or fraudulent sites; and a program of fraud alerts that allow customers to be proactive in protecting themselves and their accounts. Aside from allowing customers to do this without logging on to the BofA site, there’s obvious marketing value to letting a customer know the bank is watching their back. The bank also monitors potential fraud across all delivery channels.
Taken together, BofA obviously didn’t wait to be told what to do, and reaped the benefits, just like it reaped the benefit of offering its customers free online bill payment. At the time the bank did that, giving a billable service away was considered a bit odd, at a minimum; now, it’s considered the gold standard of customer retention. It was somewhat a matter of protecting BofA’s flanks, of course—think what it would have cost if its 27 million customers began flocking to branches for ordinary transactions—but it lit a candle in the darkness.
Why haven’t more banks come as far as BofA? “It’s a hard decision for most banks, because they have a lot of options, and they have to think about which solution is appropriate for them,” says Tubin. Luckily, most third-party providers have made it easy for them, by cutting deals with companies like PassMark; but there’s a lot of work to be done. Lucky, these systems are cheap: Between $0.15 and a dollar per user. (Contact: TowerGroup, George Tubin, 781-292-5213)